{Update: This post was edited in September 2018}
Not a day passes by without some news or the other about data breaches or security threats — be it Facebook or Apple or even the less popular businesses. How careful are you when it comes to securing your digital presence? Do you take the pain of framing complex passwords? A report suggests that well-known passwords like 1234, date of birth and all other predictable passwords such as “password” and more have led to a 20% increase in hacking activities.
Because there is no such thing as 100% cyber secure, the easiest solution is to implement two-factor authentication across personal as well as organizational applications. Two-factor authentication is the online equivalent of a combination lock whose code keeps on changing.
What is two-factor authentication?
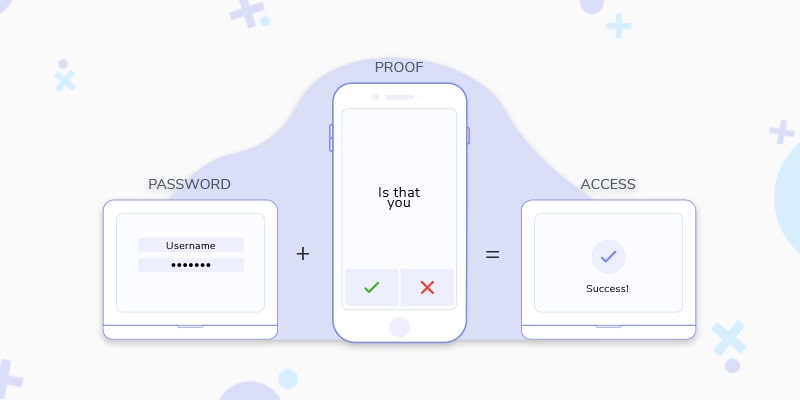
2FA or two-factor authentication is the combination of what a user has plus what they get on a registered device in order to verify their identity.

Two Factor Authentication, also known as 2 step verification or more simply put as 2FA, is an extra layer of protection that requires not only your password and username but also a second piece of identifying information. While the username and password help in identifying the user, two step verification employs a secondary piece of information which further helps in the authentication of the user.

So, even if your phone is lost, the probability of someone else having your two-way authentication information is highly unlikely.
While 2-factor authentication can work via multiple channels, one-time passwords via SMS or text codes by apps will continue to be the popular choices of security for the time being.
In markets like Indonesia and Southeast Asia, two-step verification is all the more important due to the substantial presence of the next generation of e-commerce — mobile commerce. According to a recent survey by Gemalto, 96% expect that their organization will expand their use of two-factor authentication to protect all applications in the future.
Why Two-factor Verification?
Traditionally speaking Single sign-on (SSO) architecture is not well protected nowadays. 65% use the same password everywhere, it’s like having only one key for your whole house and car. And if hackers club this technique with other hacking techniques and tools like the keylogger, social engineering, then the chances of penetration increases to 55%. Passwords can restrict the access but cannot guarantee that your account is safe from any breaches. No safety product can offer you a 100% protection but two step verification combines any two of the above three types of authentication which makes your account a less attractive target.
In order to curb such events, two-factor authentication was one of the solutions that came up and the adoption rate is staggering. Thanks to OTP authentication, access will be only given to the people will authorization rather than risking violation of data by unauthorized users or hackers. Even if the password is stolen, there is a very rare chance that the mobile phone is stolen at the same time. Even though such an event occurs these passwords have one-time use duration and expires under 10-15 minutes after triggering.
So in short, with the use of One-time password authentication, you can improve both corporate as well as customer facing security.
Thanks to OTP authentication, access is only given to the people with authorization. Even if the password is stolen, there is a very rare chance that the mobile phone is stolen at the same time. Furthermore, if the situation does arise, 2fa enables the passwords (rightly named one-time) last only for a single use and expire within a few minutes of being triggered.
How does 2FA work?
User → user name and password into your system → system sends OTP via SMS, Voice or authenticator → user feeds back into the system → user is authenticated
Types of 2FA
There are three most commonly used avenues to implement two factor authentication – Voice OTP, SMS OTP or using an Authenticator app. The first 2 are the most widely used currently in Indonesia and SEA.
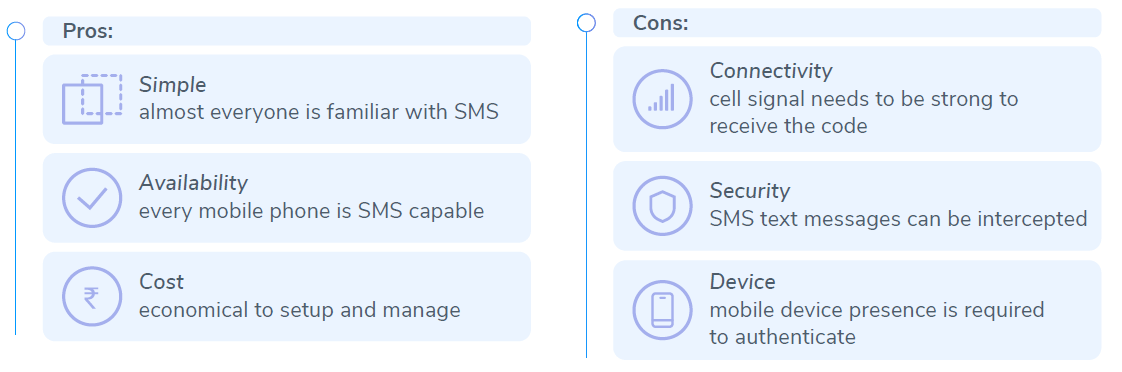
SMS OTP

SMS OTP (one time password) is the most common method of implementing 2FA. This method sends a unique 5-10 digit code via SMS to the user, after their username and password is verified. The user is required to provide this code before they are granted access.
Advantage: Easy to implement for the company. Easy to use for the customer as well.
Disadvantage: Sometimes due to traffic and operational failures, the user doesn’t receive an OTP. While most companies give you the option to ask for an OTP again in case you don’t receive it in the first go, speed is of the essence here and therefore can cause failures.
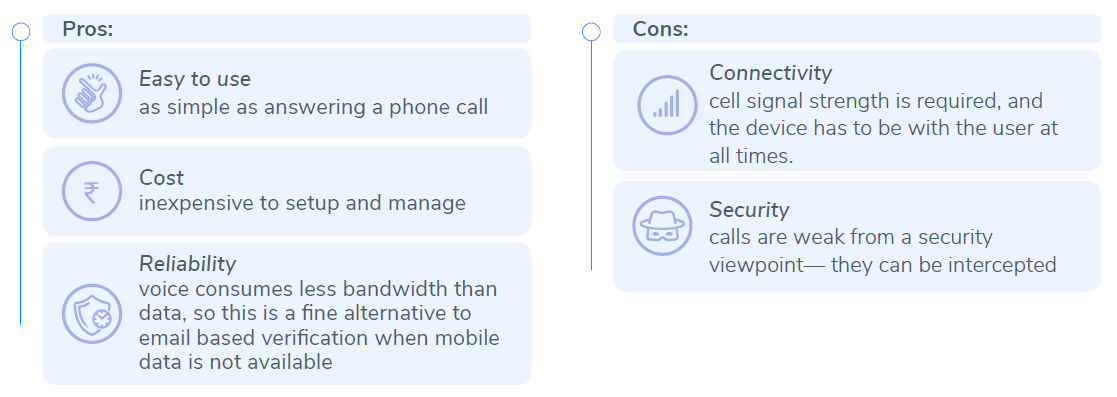
Phone call/ Voice OTP

This works in a very similar way to SMS OTP. Instead of receiving an OTP via SMS, the customer receives an automated voice call giving them the OTP. This method initiates a phone call to the user once they have verified their username and password. The call provides them with a dynamic OTP for authentication.
Advantage: Easy to use as the OTP is simply communicated through a voice call. Also, since voice consumes less bandwidth, it is for this reason that voice OTP is more reliable as compared to emails.
Disadvantage: Connectivity is one limitation as the voice OTP can only work if the device is in the possession of the user at the time of the usage. Also, security calls can be intercepted which further restricts the usage.
nOTP by Exotel
Apart from the usual OTP for authentication, Exotel also offers nOTP — a feature that allows you to authenticate and verify users without any actions from their end. Traditionally, two-factor authentication happens over SMS via OTP verification. But this method has a number of pitfalls like SMS failure, bad experience for the customer, etc. nOTP is a revolutionary product from Exotel that works without an SMS and is much faster than the typical OTP verification.
This is how it works:
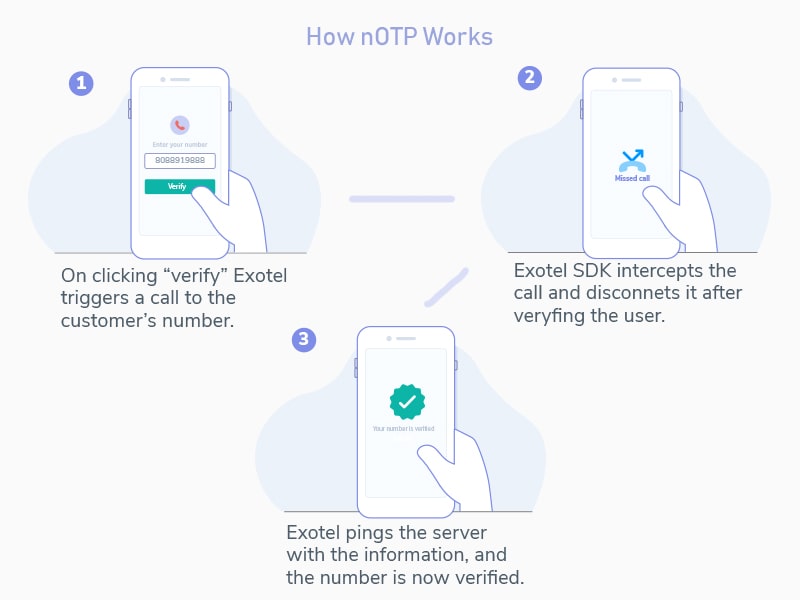
- Customer clicks the ‘verify’ button on the app
- Exotel makes an automated outbound call to the number specified in the app.
- Exotel SDK automatically intercepts the call, disconnects it and verifies the customer.
- Exotel then pings the server that the number is verified.
nOTP is currently available as an SDK for Android phones. Compared to a typical OTP mechanism, nOTP offers remarkable advantages:
- It is faster and more efficient
- Cost effective; reduces cost by up to 40%
How Exotel helps implement OTP
Since most businesses have started using 2FA now, it has become commonplace and customers don’t really see this to be an extra step anymore.
At Exotel, we have worked in easing 2FA implementation for businesses, while also bearing the customer comfort in mind. Our powerful authentication solutions are built for speed and scale.
Not every business has the same risk factor or the security needs. So why should you have to choose a “one size fits all” approach to 2FA? Our robust APIs offer a variety of authentication options such as SMS OTP, OTP over voice, OTP without SMS (nOTP) to help prioritize your needs accordingly.
Why Exotel to implement OTP

Simple: Exotel APIs work as straightforward integrations with your product/app
Cost effective: Existing Exotel account suffices and doesn’t require any new hardware or software
Easily scalable: As your customer base grows, you can easily scale with Exotel
Pay as you go: Exotel also takes care of all the infrastructure updates so you don’t have to worry about the maintenance.




 +91-8088919888
+91-8088919888 +1-(718) 354-8866
+1-(718) 354-8866 +61-2-8073-0559
+61-2-8073-0559 +62-215-098-4960
+62-215-098-4960 +60-3-2771-2799
+60-3-2771-2799 +65-6951-5460
+65-6951-5460
No Comments